Why Cybersecurity in Healthcare Matters More Than Ever
Cybersecurity in healthcare protects patient data, medical devices, and hospital systems from digital attacks that can disrupt care and endanger lives. It encompasses the policies, technologies, and practices that safeguard Protected Health Information (PHI) and ensure healthcare operations continue safely in an increasingly connected world.
Key Reasons Healthcare Cybersecurity is Critical:
- Patient Safety – Cyberattacks can disable medical devices, delay surgeries, and force patient diversions
- Data Protection – PHI is worth 10-20 times more than credit card data on the dark web
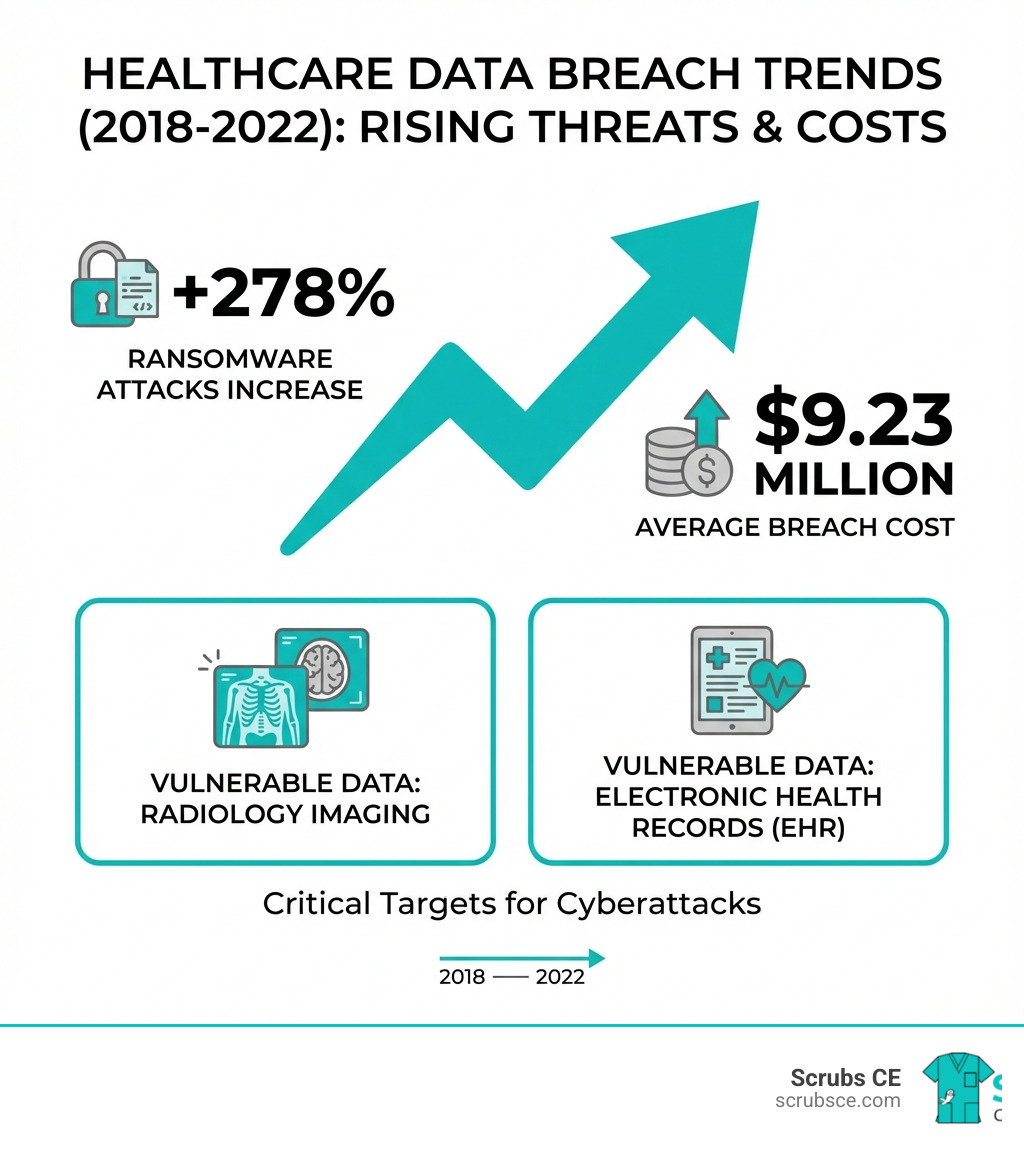
- Financial Impact – Healthcare breaches cost an average of $9.23 million, more than double other industries, according to the 2021 Cost of a Data Breach Report
- Regulatory Compliance – HIPAA violations can result in penalties up to $1.81 million per year
- Operational Continuity – Ransomware attacks can shut down hospitals for weeks or months
Healthcare delivery organizations face a unique challenge. They operate in an environment where patient care cannot stop, yet they manage highly valuable personal information while relying on complex networks of connected medical devices. As of January 2022, the U.S. Department of Health and Human Services was investigating 860 data breaches reported in just 24 months, each exposing the protected health information of 500 or more individuals.
The stakes are exceptionally high. When a hospital’s electronic health records become inaccessible during a ransomware attack, critical patient data needed for surgeries and treatments disappears. Appointments get cancelled. Patients get diverted to other facilities. In some cases, lives are at risk.
The threat landscape has intensified rapidly. Ransomware attacks now account for nearly 50% of all healthcare data breaches, with threat actors demanding average payments of $910,335 in 2021. Meanwhile, 86% of covered healthcare breaches stem from human errors, web application attacks, and system intrusions involving stolen credentials.
Healthcare organizations also face unique technical vulnerabilities. Legacy medical devices running outdated software create entry points for hackers. The rapid shift to telehealth and remote work expanded attack surfaces. Internet-connected infusion pumps, heart monitors, and other Internet of Medical Things (IoMT) devices often lack robust security protocols yet connect directly to hospital networks.
The human factor compounds these technical challenges. Healthcare workers face intense workloads while managing sensitive data daily. Research shows a statistically significant correlation between workload and the probability of staff opening phishing emails. Environmental factors affecting practitioners’ security behaviors often outweigh their security intentions.
“With its focus on caring for people, the Healthcare and Public Health sector touches each of our lives in powerful ways,” notes the Cybersecurity and Infrastructure Security Agency. Yet much of this work now exists in the digital world, where disruptions can impact patient safety, create openings for identity theft, and expose intellectual property.
I’m Zita Ewert, and through my work in continuing education for healthcare professionals, I’ve seen how critical ongoing training is for cybersecurity in healthcare awareness and compliance. Understanding these threats and implementing proper safeguards isn’t just an IT issue—it’s a fundamental component of patient safety that every healthcare professional must grasp.
Basic Cybersecurity in healthcare glossary:
The Modern Threat Landscape: Common Attacks and Their Impact
The digital change in healthcare, while offering immense benefits for patient care and operational efficiency, has simultaneously cast a long shadow of increased cyber risk. Healthcare organizations are not merely targets; they are often prime targets. The consequences of these attacks extend far beyond financial loss, directly impacting patient well-being and the very fabric of healthcare delivery.
The Office for Civil Rights of the U.S. Department of Health and Human Services (HHS) was investigating a staggering 860 data breaches in a 24-month period leading up to January 2022, each affecting 500 or more individuals. This demonstrates the relentless assault on our healthcare systems. The financial toll is equally alarming: the average cost of a healthcare breach soared to $9.23 million, more than double the average across all other industries. This stark reality underscores the urgent need for robust cybersecurity in healthcare.
Understanding the Most Prevalent Cyberattacks in Healthcare
To effectively defend against cyber threats, we must first understand them. In healthcare, certain attack types are particularly common and devastating.
Ransomware Attacks: This is perhaps the most feared cyberattack in healthcare, accounting for almost 50% of all data breaches in the sector in 2020, according to HHS Office of Information Security. Ransomware is malicious software that locks users out of their systems, devices, or files until a ransom is paid. The insidious nature of ransomware is that even if a ransom is paid, there’s no guarantee of regaining access, nor that the data won’t be sold or leaked. In 2021, threat actors extorted an average of $910,335 in ransomware payments from healthcare organizations. The impact can be catastrophic, leading to widespread system outages, cancellation of appointments, and diversion of patients, as seen in a Czech hospital that had to postpone surgeries due to an attack.
Phishing and Social Engineering: These tactics exploit the human element. Phishing involves cybercriminals attempting to trick individuals into divulging sensitive information or downloading malicious software by masquerading as legitimate entities. They often use deceptive emails, texts, or phone calls. A statistically significant positive correlation exists between workload and the probability of healthcare staff opening a phishing email, highlighting the vulnerability of overworked healthcare professionals. These attacks often lead to credential theft, where attackers steal login information to gain unauthorized access to systems.
Denial-of-Service (DoS) Attacks: A DoS attack aims to overwhelm a system with traffic, causing it to crash and become unavailable. While not always directly leading to data theft, it can severely disrupt critical services, websites, and internal operations. This type of attack can be used as a distraction while other malicious activities are carried out, or simply to cause chaos and disrupt patient care.
System Intrusions: This broad category includes unauthorized access to IT systems through various means, often facilitated by stolen credentials or exploiting vulnerabilities in web applications. Once inside, attackers can steal data, plant malware, or disrupt operations.
The top 3 impacts of a successful cyberattack on a hospital are:
- Disruption of Patient Care: Inaccessible patient data, disabled medical devices, and cancelled procedures.
- Financial Fallout: High costs for recovery, regulatory fines, and reputational damage.
- Compromised Patient Safety: Delays in critical treatments, misdiagnosis due to unavailable records, and potential loss of life.
Why Healthcare is a Prime Target for Cybercriminals
The healthcare industry is a magnet for cybercriminals for several compelling reasons, primarily centered around the immense value and sensitivity of the data it holds.
Value of PHI: Protected Health Information (PHI) is a goldmine for cybercriminals. It contains a wealth of personal data—names, addresses, social security numbers, medical history, insurance information—that can be used for various illicit activities. On the black market, PHI is estimated to be worth 10-20 times the value of credit card data. This “richness of personal information” makes each medical record fetch hundreds of dollars.
Identity Theft Potential: With comprehensive PHI, criminals can commit identity theft, opening new lines of credit, filing fraudulent tax returns, or even obtaining medical services under someone else’s name.
Healthcare Insurance Fraud: Stolen PHI is invaluable for healthcare insurance fraud, allowing criminals to create fake claims, purchase medical equipment, or obtain prescription drugs.
Criticality of Services: Beyond data, the very nature of healthcare services makes organizations vulnerable. Hospitals cannot afford downtime; patient lives depend on continuous operation. This urgency often makes healthcare entities more likely to pay ransoms in a desperate attempt to restore services quickly, making them attractive targets for ransomware gangs. The disruption in the work of healthcare facilities and the inaccessibility of patient data required for critical procedures can, literally, cost lives.
Key Vulnerabilities: Where Healthcare Systems Are Weakest
Despite the critical importance of cybersecurity in healthcare, the sector faces significant inherent vulnerabilities. These weaknesses often stem from a complex interplay of outdated technology, human factors, and regulatory challenges, creating fertile ground for cyberattacks.
Securing the Internet of Medical Things (IoMT)
The proliferation of connected medical devices, collectively known as the Internet of Medical Things (IoMT), has revolutionized patient care but introduced a new frontier of cybersecurity risks. These devices range from infusion pumps and heart monitors to sophisticated Radiology equipment and even critical infrastructure like air filtration systems.
Legacy Medical Devices: A major challenge is that many older medical devices still in use were not designed with cybersecurity in mind. They often run outdated software, which creates vulnerable points of entry. These “legacy devices” may lack the necessary security features, cannot be easily patched, and can become a major point of entry for hackers into a hospital’s network.
Complexity and Interoperability Challenges: Medical devices are complex systems, making them difficult to secure due due to their multiple components, interfaces, and connectivity options. Furthermore, the need for interoperability—devices communicating with each other and with Electronic Health Records (EHR) systems—creates additional pathways for potential exploitation if not properly secured. While healthcare providers have improved the security of EHRs, hackers are now increasingly targeting medical devices.
Supply Chain Risks: Healthcare providers often have “limited end-to-end visibility” across their medical device network and supply chain. This lack of transparency limits proper detection and response, as vulnerabilities can be introduced at any point from manufacturing to deployment and maintenance.
The Human Factor in Cybersecurity in healthcare
Even the most advanced technological defenses can be undermined by human error. In cybersecurity in healthcare, the human element is a critical vulnerability point.
Employee Training Gaps and Social Engineering Susceptibility: Healthcare staff, often under immense pressure and juggling multiple responsibilities, may not receive adequate or up-to-date cybersecurity training. This leaves them susceptible to social engineering tactics like phishing, where attackers manipulate individuals into revealing sensitive information or performing actions that compromise security. Studies have shown that a significant portion of healthcare breaches are caused by errors, web application attacks, and system intrusions, including those involving credential theft, underscoring the role of human vigilance.
Importance of Security Awareness: Continuous, relevant security awareness training is paramount. Staff need to understand the latest threats, recognize phishing attempts, and follow secure practices consistently. Without this, even basic security protocols can be bypassed. For example, a statistically significant positive correlation exists between workload and the probability of healthcare staff opening a phishing email, highlighting the need for training that acknowledges operational realities.
Human Error Statistics: The majority of information security incidents are related to human error. This isn’t just about malicious intent; it’s often about mistakes, lack of knowledge, or being overwhelmed. We must foster a culture where reporting potential incidents is encouraged, not penalized, allowing for learning and improvement.
Systemic and Regulatory Gaps
Beyond devices and people, systemic and regulatory gaps create underlying vulnerabilities in cybersecurity in healthcare.
Outdated Software and Lack of Patching: Many healthcare systems, including critical infrastructure and even some medical devices, run on outdated software that no longer receives security updates or patches. This creates known vulnerabilities that attackers can easily exploit. The rapid pace of digital change often outstrips the ability to update or replace these systems, leading to a permanent state of vulnerability.
Inconsistent Compliance and Regulation Gaps: While the Food and Drug Administration (FDA) has taken significant steps to enforce medical device regulations in recent years, there is still inconsistent compliance by medical device manufacturers and healthcare providers. This means that devices may enter the market or be used in clinical settings without adequate security considerations. Furthermore, the sheer complexity of the healthcare ecosystem, with its myriad of interconnected systems and third-party vendors, makes comprehensive regulatory oversight challenging. Resource limitations, particularly for smaller healthcare organizations, also hinder the adoption of robust security measures.
The Regulatory Framework: HIPAA and Compliance Obligations
In the United States, the Health Insurance Portability and Accountability Act (HIPAA) stands as the cornerstone of patient data protection. Enacted in 1996, HIPAA’s Administrative Simplification provisions aimed to standardize electronic healthcare transactions while simultaneously recognizing the need to safeguard the privacy of health information. For us in healthcare, understanding and adhering to HIPAA is not just a legal obligation; it’s a fundamental aspect of ethical patient care and robust cybersecurity in healthcare.
HIPAA comprises several key components, two of which are central to cybersecurity: the Privacy Rule and the Security Rule, alongside the Breach Notification Rule.
Core Requirements of the HIPAA Security Rule
The HIPAA Security Rule establishes national standards to protect individuals’ electronic Protected Health Information (ePHI). It mandates compliance with administrative, physical, and technical safeguards to ensure ePHI’s confidentiality, integrity, and security.
- Protecting ePHI: The rule requires covered entities to ensure the confidentiality, integrity, and availability of all ePHI they create, receive, maintain, or transmit. This means preventing unauthorized access, ensuring data isn’t altered or destroyed improperly, and making sure it’s accessible when needed by authorized personnel.
- Ensuring Confidentiality and Integrity: Confidentiality means ePHI is not available or disclosed to unauthorized persons. Integrity means ePHI has not been altered or destroyed in an unauthorized manner.
- Risk Analysis: Covered entities must conduct accurate and thorough assessments of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of ePHI. This ongoing process helps identify weaknesses that could lead to data breaches.
- Access Control: This is a crucial technical safeguard requiring policies and procedures that allow only authorized persons to access ePHI. This includes implementing unique user IDs, emergency access procedures, automatic logoffs, and encryption/decryption mechanisms.
The official HIPAA Security Rule details these requirements, outlining both “required” and “addressable” implementation specifications that covered entities must adopt. We must ensure our systems, from patient records to Radiology imaging, are secured in accordance with these standards.
Legal and Financial Consequences of Non-Compliance
Failure to comply with HIPAA regulations can lead to severe repercussions, impacting an organization’s finances, reputation, and most importantly, patient trust.
- Civil Monetary Penalties: The Office for Civil Rights (OCR) of the HHS can impose significant penalties for HIPAA violations. These penalties can reach $1.81 million per calendar year, depending on the severity and nature of the violation. These fines are designed to deter non-compliance and cover the costs associated with investigating and resolving breaches.
- Corrective Action Plans: Beyond fines, organizations may be required to implement extensive corrective action plans, which can be costly and disruptive to operations. These plans aim to address the root causes of non-compliance and strengthen security postures.
- Reputational Damage: A data breach or HIPAA violation can severely damage an organization’s reputation. Public trust is paramount in healthcare, and a breach can erode that trust, leading to patient attrition and negative public perception.
- Patient Trust Erosion: When patient data is compromised, individuals lose faith in the healthcare system’s ability to protect their most sensitive information. This can have long-lasting effects on patient engagement and willingness to share necessary medical details.
While HIPAA is the primary U.S. regulation, global privacy laws like GDPR (General Data Protection Regulation) also impact healthcare organizations that handle data from individuals in the European Union. We must consider all relevant regulatory frameworks to ensure comprehensive protection.
Building a Resilient Strategy for Cybersecurity in healthcare
In the face of persistent and evolving threats, healthcare organizations must move beyond reactive measures and accept a proactive, resilient cybersecurity in healthcare strategy. This involves not just deploying technology but fostering a culture of security, continuous improvement, and preparedness.
Essential Best Practices and Solutions
A robust cybersecurity strategy is built on a foundation of proven best practices and smart technological solutions. Here are some essential elements:
- Multi-Factor Authentication (MFA): This is a critical layer of security that requires users to provide two or more verification factors to gain access to an account. This could be a password and a fingerprint, or a password and a code sent to a mobile device. Implementing MFA, especially phishing-resistant MFA, for remote access and all sensitive systems drastically reduces the risk of credential theft leading to a breach.
- Zero Trust Architecture: Instead of assuming trust within the network perimeter, a Zero Trust model operates on the principle of “never trust, always verify.” Every user, device, and application attempting to access resources must be authenticated and authorized, regardless of their location. This granular approach significantly improves security, particularly in complex healthcare environments with numerous interconnected devices and remote workers.
- Network Segmentation: Dividing the network into smaller, isolated segments helps contain the impact of a breach. If one segment is compromised (e.g., an IoMT device network), attackers cannot easily move laterally to other critical systems like EHRs or Radiology data servers. This strategy limits the “blast radius” of an attack.
- Regular System Updates and Patching: Keeping all software, operating systems, applications, and firmware up-to-date is fundamental. Patches often address known vulnerabilities that attackers actively exploit. Neglecting updates creates easy entry points for cybercriminals.
- Comprehensive Employee Training and Awareness: As we’ve seen, human error is a significant factor in breaches. Mandatory, regular training on identifying phishing attempts, strong password practices, secure remote work protocols, and the importance of data privacy empowers staff to be the first line of defense. Simulated phishing attacks can reinforce this training effectively.
Advanced Technologies and Future-Proofing
Looking ahead, advanced technologies offer powerful tools to bolster cybersecurity in healthcare.
Role of Artificial Intelligence (AI) and Machine Learning (ML): AI and ML can be leveraged for advanced threat detection and analysis. They can identify anomalous behaviors, predict potential attacks, and sift through vast amounts of data to uncover subtle indicators of compromise far more efficiently than human analysts. AI can help in real-time monitoring and automated responses.
Security Automation: Automating routine security tasks, such as vulnerability scanning, patch deployment, and incident triage, frees up valuable human resources and ensures consistent, rapid responses to threats.
Securing Remote Work Environments: The rapid shift to remote work during the pandemic highlighted vulnerabilities in telehealth and home-based care. Best practices for preventing ransomware attacks, as advised by CISA, include requiring multi-factor authentication for remote access and enabling strong spam filters to prevent phishing emails. Organizations must ensure secure VPNs, endpoint protection, and robust remote access policies for all staff, including those accessing Radiology systems from home.
The Importance of Business Continuity and Incident Response
In cybersecurity in healthcare, preventing all attacks is an admirable goal, but preparing for the inevitable is just as crucial. A robust business continuity plan (BCP) and an effective incident response plan (IRP) are non-negotiable.
Ensuring Service Continuity: A BCP outlines how an organization will maintain essential functions during and after a cyberattack. This includes strategies for hardware failover, data recovery, and backups to off-site systems or cloud platforms. The goal is to minimize downtime and ensure that patient care can continue, even if systems are compromised.
Data Recovery: Regular and tested backups are the lifeline for recovery. In the event of a ransomware attack, being able to restore systems from clean backups can prevent the need to pay a ransom and significantly reduce recovery time.
Post-Incident Analysis and Improving Response Plans: Responding to a cybersecurity incident is only the beginning. What happens after the incident is resolved is just as important. Thorough post-incident reviews, involving all relevant stakeholders, are essential for understanding root causes, assessing the effectiveness of the response, and identifying areas for improvement. This analysis helps us improve our IRPs, update policies and procedures, improve detection tools, and refine staff training programs. Continuous improvement is key to staying ahead of evolving threats and meeting regulatory requirements.
Conclusion: A Collective Responsibility for Patient Safety
The landscape of cybersecurity in healthcare is complex and constantly shifting, but one truth remains constant: safeguarding patient safety is our paramount responsibility. We’ve explored the primary threats, from pervasive ransomware attacks to the vulnerabilities inherent in legacy medical devices and the human factor. We’ve digd into the critical role of regulations like HIPAA and the severe consequences of non-compliance.
Building a resilient cybersecurity posture requires a multi-faceted approach. It’s about implementing essential best practices like MFA and Zero Trust, leveraging advanced technologies like AI for threat detection, and, crucially, having robust business continuity and incident response plans.
Cybersecurity in healthcare is not solely the domain of IT professionals; it’s a team sport. Every healthcare worker, from administrators to physicians, nurses, and Radiology technicians, plays a vital role in protecting sensitive patient data and ensuring the continuity of care. Our collective vigilance, adherence to protocols, and commitment to continuous learning are our strongest defenses.
At Scrubs CE, we believe in empowering healthcare professionals with the knowledge they need to steer this evolving digital world safely and effectively. Continuous education is not just about meeting licensure requirements; it’s about staying ahead of threats, protecting our patients, and upholding the integrity of our healthcare systems.
The future of healthcare is undeniably digital, and with that comes new risks. By understanding these challenges and embracing a proactive, collaborative approach to cybersecurity, we can ensure that technological advancements continue to improve patient care without compromising safety.
Explore continuing education courses for Radiology professionals to stay informed and strengthen our collective defense against cyber threats.


Recent Comments